SELinux in Linux interview questions
Understanding SELinux in RHEL 9: A Beginner-Friendly Guide with interview Questions.
Security-Enhanced Linux (SELinux) is a feature built into the Linux kernel to provide an additional layer of security. It controls how processes, users, and applications access files and resources. In RHEL 9, SELinux plays a crucial role in ensuring system security by enforcing rules that prevent unauthorized actions.
If you’re new to SELinux, don’t worry! This guide explains everything step-by-step and includes lab commands so you can practice hands-on.
What is SELinux?
Imagine your computer is like a library. In this library, only authorized people (processes and users) can access certain books (files). SELinux acts like a strict librarian, ensuring that every person follows the rules set for the library.
Here’s how SELinux achieves this:
- Policies: Rules that define what actions are allowed or denied.
- Contexts: Labels attached to files and processes that describe their role.
- Modes: Settings that determine how strict SELinux should be.
Modes of SELinux
SELinux can operate in three different modes:
- Enforcing Mode:
- SELinux policies are active and violations are blocked.
- Example: If an unauthorized user tries to access a sensitive file, the action is denied, and a log entry is created.
- Permissive Mode:
- SELinux policies are checked, but violations are only logged, not blocked.
- Useful for troubleshooting because it lets you see what would be denied in enforcing mode.
- Disabled Mode:
- SELinux is turned off completely. This is not recommended because it removes a critical layer of security.
How to Check the Current SELinux Status
To see if SELinux is enabled and which mode it’s running in, use the sestatus command:
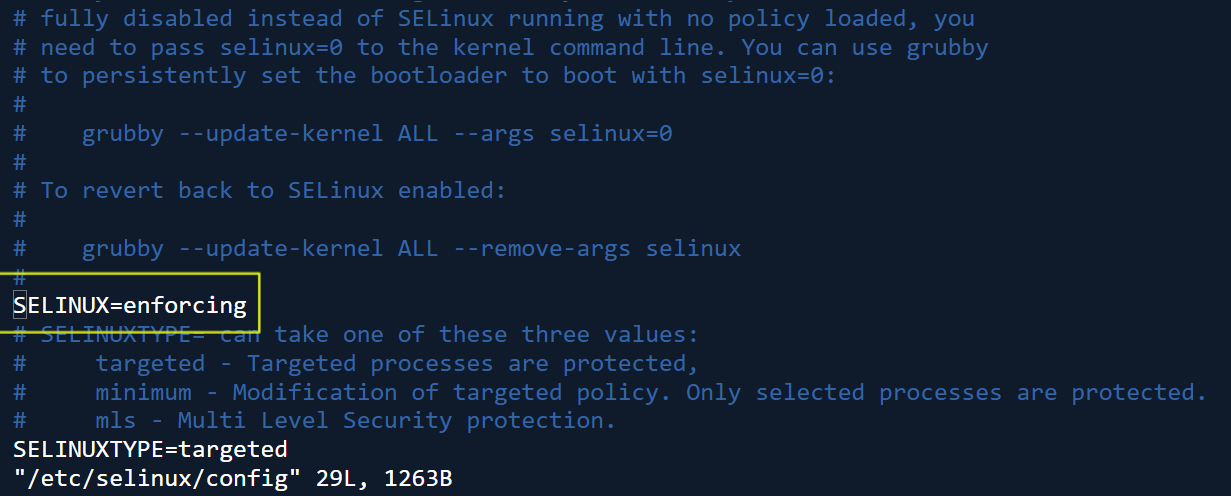
# vi /etc/selinux/config
Open this file to check SELinux Status:
To check SELinux status use sestatus command:
Example Output:

The output from the sestatus command, which provides detailed information about the current state and configuration of SELinux. Let’s break down each line to understand what it means:
1. SELinux status: enabled
- Explanation: This shows that SELinux is active on the system. If it were disabled, SELinux would not enforce any policies or log access violations.
- Why important?: It confirms that SELinux is functioning as a security mechanism on the system.
2. SELinuxfs mount: /sys/fs/selinux
- Explanation: SELinux uses a virtual filesystem,
selinuxfs, to interact with its configuration and policies. This line shows the mount point of that filesystem. - Why important?: Tools and commands use this filesystem to check SELinux status and settings. It’s like the “control panel” for SELinux within the kernel.
3. SELinux root directory: /etc/selinux
- Explanation: This is the directory where SELinux configuration files and policies are stored.
- Why important?: Files in
/etc/selinuxdefine which policy is used (e.g., targeted or MLS) and the system’s default SELinux mode. This is where administrators can modify configurations.
4. Loaded policy name: targeted
- Explanation: This indicates the active SELinux policy on the system. The targeted policy is the default in RHEL and protects specific services, leaving most user applications unconfined.
- Why important?: The targeted policy provides a balance between security and usability, focusing protection on critical services like
httpd,sshd, anddns.
5. Current mode: enforcing
- Explanation: The system is running in enforcing mode, meaning SELinux policies are actively blocking unauthorized actions and logging them.
- Why important?: Enforcing mode is the most secure mode and is suitable for production systems.
6. Mode from config file: enforcing
- Explanation: This indicates the SELinux mode specified in the
/etc/selinux/configfile. It determines the mode the system should use after a reboot. - Why important?: If this value differs from the current mode, it means the mode was temporarily changed using the
setenforcecommand.
7. Policy MLS status: enabled
- Explanation: The Multi-Level Security (MLS) policy feature is enabled. MLS enforces strict data separation based on security levels (e.g., Top Secret, Secret, Confidential).
- Why important?: While enabled, it is typically not used in the targeted policy. MLS is more common in military or highly sensitive environments.
8. Policy deny_unknown status: allowed
- Explanation: This controls how SELinux handles unknown object classes or permissions. When set to “allowed,” the system permits access for unknown items. This is common in targeted policies for compatibility.
- Why important?: Ensures system functionality even if SELinux encounters an undefined class or permission.
9. Memory protection checking: actual (secure)
- Explanation: SELinux includes memory protection features to ensure that processes can’t access memory in unauthorized ways. “Actual (secure)” means these protections are actively being enforced.
- Why important?: Prevents attacks like buffer overflows or code injection that target process memory.
10. Max kernel policy version: 33
- Explanation: This indicates the highest version of the SELinux policy format that the kernel supports. Policies are versioned to support new features as SELinux evolves.
- Why important?: Ensures compatibility between the kernel and the loaded SELinux policy.
How to Change SELinux Modes
Sometimes, you might need to switch SELinux to permissive mode for troubleshooting or testing. You can do this temporarily or permanently.
Temporary Change
To change the mode only until the next reboot, use the setenforce command:
####Example Command######
setenforce 0 # Switches to permissive mode
setenforce 1 # Switches back to enforcing mode

Permanent Change
If you want the mode to remain changed after a reboot, edit the SELinux configuration file:
####Example Command######
#vim /etc/selinux/config

SELinux Contexts: The Key to Control
Every file and process in SELinux has a context. Think of contexts as labels that describe what a file or process is allowed to do.
SELinux contexts are labels assigned to files, processes, and resources to control access based on security policies. Each context consists of four components: user, role, type, and level. The type is the most critical part, as it defines what a process or user can do with an object. For example, files served by Apache must have the type httpd_sys_content_t. SELinux enforces rules to ensure that only authorized interactions occur between these contexts. If a context is incorrect, SELinux may deny access, which can be resolved by restoring the default context using commands like restorecon.
How to View Contexts
To see the SELinux context of directory, use the ls command with the -Zd option:
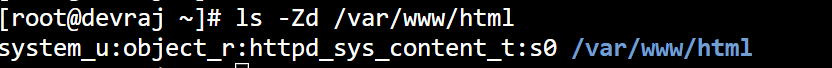
Explanation of above output is here,
1. system_u (SELinux User)
- What it means: The SELinux user associated with this object.
- Details:
system_uis a special user reserved for system processes and files.- It indicates that the directory is managed by the system and not tied to a human user.
2. object_r (SELinux Role)
- What it means: The role defines how SELinux roles interact with objects (files, directories, etc.).
- Details:
object_ris a generic role for non-process objects, like files and directories.- This role is common for files and doesn’t usually need customization.
3. httpd_sys_content_t (SELinux Type)
- What it means: The type (or domain) is the most important part of the context. It defines how this object can be accessed and by which processes.
- Details:
httpd_sys_content_tis the type for content served by the Apache HTTP Server (httpd).- Files and directories with this type can be read by the
httpdprocess, allowing the server to deliver web pages. - Other processes outside of the
httpddomain cannot access these files unless explicitly allowed by SELinux policies.
4. s0 (SELinux Level)
- What it means: The SELinux level is used in Multi-Level Security (MLS) systems to define access levels.
- Details:
s0is the default sensitivity level, meaning no specific sensitivity restrictions are applied.- In most targeted policies (like the one in use here), MLS features are enabled but not actively used.
How to Change Contexts
If a file doesn’t have the right context, SELinux will block access. To fix this, use the chcon command:
Restoring Default Contexts
If you’re unsure about the correct context, restore the default one using restorecon:
####Example Command######
# restorecon -Rv /var/www/html
Using SELinux Booleans for Flexibility
SELinux Booleans are like on/off switches that control specific features. For example, you might need to let the Apache web server connect to a database.
SELinux Booleans are toggleable settings that provide flexibility in how SELinux policies are applied. They act like on/off switches, enabling or disabling specific permissions without modifying the overall policy. For example, the Boolean httpd_can_network_connect allows the Apache web server to make network connections when enabled. Administrators can view all Booleans with getsebool -a and change their state using setsebool, adding the -P flag to make changes permanent. Booleans simplify system management by letting users adjust permissions for common scenarios dynamically while maintaining strict security controls elsewhere in the system.
How to View Booleans
To see all available SELinux Booleans, use:
#getsebool -a
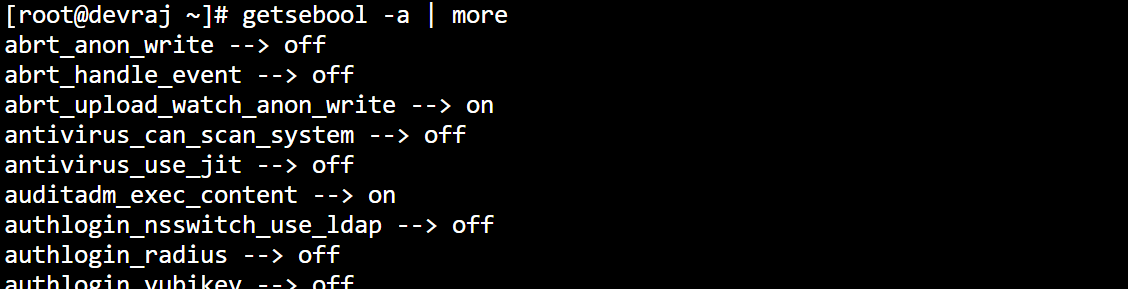
How to Change Booleans
To allow Apache to connect to a database, enable the httpd_can_network_connect_db Boolean:
![]()
The -P option makes the change permanent.
Troubleshooting SELinux Issues
When SELinux blocks something, it logs the event. These logs are invaluable for troubleshooting.
Viewing Logs
To see SELinux-related logs:
####Example Command######
#grep ‘SELinux’ /var/log/audit/audit.log
Generating Reports
Use the sealert command to analyze logs and suggest solutions:
####Example Command######
#sealert -a /var/log/audit/audit.log
SELinux Interview Questions with Answers for a Linux System Administrator
1. What is SELinux, and why is it important?
Answer:
SELinux (Security-Enhanced Linux) is a security module integrated into the Linux kernel that enforces mandatory access control (MAC). It restricts how processes interact with files, users, and system resources based on policies. SELinux is critical because it mitigates the damage caused by misconfigurations or exploited vulnerabilities, ensuring unauthorized access or actions are blocked.
2. What are the three modes of SELinux, and how do they differ?
Answer:
- Enforcing: SELinux policies are applied, and unauthorized actions are blocked.
- Permissive: Policies are not enforced, but violations are logged for debugging.
- Disabled: SELinux is turned off, and no policies are applied.
Enforcing mode provides maximum security, while permissive mode is useful for troubleshooting.
3. What is the difference between the targeted and MLS policies in SELinux?
Answer:
- Targeted Policy: Protects specific services (like
httpdorsshd) while leaving most processes unconfined. It is the default policy in RHEL and suitable for general use. - MLS Policy: Implements Multi-Level Security for strict data classification and separation, often used in high-security environments such as military systems.

Conclusion
SELinux might seem complex at first, but it’s a powerful tool for securing your system. By learning how to manage contexts, Booleans, and modes, you can control access precisely and troubleshoot effectively.
Remember, SELinux isn’t just about blocking unauthorized actions—it’s about understanding and enforcing the security rules that keep your system safe. Start practicing the lab commands to solidify your learning!

Cybersecurity Architect | Cloud-Native Defense | AI/ML Security | DevSecOps
With over 23 years of experience in cybersecurity, I specialize in building resilient, zero-trust digital ecosystems across multi-cloud (AWS, Azure, GCP) and Kubernetes (EKS, AKS, GKE) environments. My journey began in network security—firewalls, IDS/IPS—and expanded into Linux/Windows hardening, IAM, and DevSecOps automation using Terraform, GitLab CI/CD, and policy-as-code tools like OPA and Checkov.
Today, my focus is on securing AI/ML adoption through MLSecOps, protecting models from adversarial attacks with tools like Robust Intelligence and Microsoft Counterfit. I integrate AISecOps for threat detection (Darktrace, Microsoft Security Copilot) and automate incident response with forensics-driven workflows (Elastic SIEM, TheHive).
Whether it’s hardening cloud-native stacks, embedding security into CI/CD pipelines, or safeguarding AI systems, I bridge the gap between security and innovation—ensuring defense scales with speed.
Let’s connect and discuss the future of secure, intelligent infrastructure.


